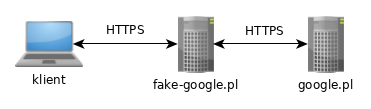
 We can verify if the lure has been created successfully by typing the following command: Thereafter, we can get the link to be sent to the victim by typing the following: We can send the link generated by various techniques. This is a feature some of you requested. This ensures that the generated link is different every time, making it hard to write static detection signatures for. WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes.
We can verify if the lure has been created successfully by typing the following command: Thereafter, we can get the link to be sent to the victim by typing the following: We can send the link generated by various techniques. This is a feature some of you requested. This ensures that the generated link is different every time, making it hard to write static detection signatures for. WebEvilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes.  After importing, when the attacker refreshes the instagram.com page, we can see that the attacker is logged into the victims account: NB: The attacker can only be logged on to the victims account as long as the victim is logged into their account. This blog tells me that version 2.3 was released on January 18th 2019. Typehelporhelp
After importing, when the attacker refreshes the instagram.com page, we can see that the attacker is logged into the victims account: NB: The attacker can only be logged on to the victims account as long as the victim is logged into their account. This blog tells me that version 2.3 was released on January 18th 2019. Typehelporhelp  We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials.
We will also find out how to use it to bypass two-factor authentication and steal Instagram login credentials. 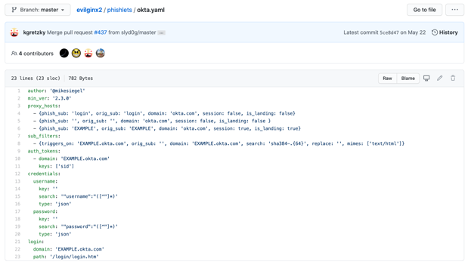 These attacks threaten more than just email environments, as other services such as Okta, Citrix, and others are at risk of the same types of attack. Cybersecurity is always evolving, and the abilities of threat actors to circumvent MFA does not come as a surprise. Copyright 2023 Black Hat Ethical Hacking All rights reserved, https://www.linkedin.com/company/black-hat-ethical-hacking/, get an extra $10 to spend on servers for free, Offensive Security Tool: Bypass Url Parser. As such, there may be a detection opportunity when the threat actor imports cookies into their own browser and the user agent switches while the SessionId remains the same. Finally, we will build and launch a combat server, tweak it, and go phishing! If you want to add IP ranges manually to your blacklist file, you can do so by editing blacklist.txt file in any text editor and add the netmask to the IP: You can also freely add comments prepending them with semicolon: You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. evilginx2 google phishlet. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. Such feedback always warms my heart and pushes me to expand the project. I hope some of you will start using the new templates feature. Find Those Ports And Kill those Processes. https://github.com/kgretzky/evilginx2.
These attacks threaten more than just email environments, as other services such as Okta, Citrix, and others are at risk of the same types of attack. Cybersecurity is always evolving, and the abilities of threat actors to circumvent MFA does not come as a surprise. Copyright 2023 Black Hat Ethical Hacking All rights reserved, https://www.linkedin.com/company/black-hat-ethical-hacking/, get an extra $10 to spend on servers for free, Offensive Security Tool: Bypass Url Parser. As such, there may be a detection opportunity when the threat actor imports cookies into their own browser and the user agent switches while the SessionId remains the same. Finally, we will build and launch a combat server, tweak it, and go phishing! If you want to add IP ranges manually to your blacklist file, you can do so by editing blacklist.txt file in any text editor and add the netmask to the IP: You can also freely add comments prepending them with semicolon: You can now make any of your phishlet's sub_filter entries optional and have them kick in only if a specific custom parameter is delivered with the phishing link. evilginx2 google phishlet. Evilginx2 Phishlets version (0.2.3) Only For Testing/Learning Purposes Google recaptcha encodes domain in base64 and includes it in co parameter in GET request. Such feedback always warms my heart and pushes me to expand the project. I hope some of you will start using the new templates feature. Find Those Ports And Kill those Processes. https://github.com/kgretzky/evilginx2.  Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. You can specify {from_name} and {filename} to display a message who shared a file and the name of the file itself, which will be visible on the download button. Pre-phish HTML templates add another step in, before the redirection to phishing page takes place. Can Help regarding projects related to Reverse Proxy. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. Make sure Your Server is located in United States (US). https://breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens/, https://www.youtube.com/watch?v=PNXVhqqcZ8Y, https://www.youtube.com/watch?reload=9&v=GDVxwX4eNpU, https://www.youtube.com/watch?v=QRyinxNY0fk&t=347s. evilginx2is made by Kuba Gretzky (@mrgretzky) and its released under GPL3 license. Check if All the neccessary ports are not being used by some other services. May the phishing season begin! Increased the duration of whitelisting authorized connections for whole IP address from 15 seconds to 10 minutes. https://github.com/kgretzky/evilginx2. Of course this is a bad example, but it shows that you can go totally wild with the hostname customization and you're no longer constrained by pre-defined phishlet hostnames. Be Creative when it comes to bypassing protection. They are the building blocks of the tool named evilginx2. You can also escape quotes with \ e.g. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. Welcome back everyone! You can now import custom parameters from file in text, CSV and JSON format and also export the generated links to text, CSV or JSON. After adding all the records, your DNS records should look something like this: After the Evilginx2 is installed and configured, we must now set up and enable the phishlet in order to perform the attack. Please evilginx2will tell you on launch if it fails to open a listening socket on any of these ports. Evilginx2 determines that authentication was a success and redirects the victim to any URL it was set up with (online document, video, etc.). Phishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. If you have any ideas/feedback regarding Evilginx or you just want to say "Hi" and tell me what you think about it, do not hesitate to send me a DM on Twitter. The very first thing to do is to get a domain name for yourself to be able to perform the attack. The user may be tipped off by the additional request for authentication, or by the fact that whatever was promised to them in the phishing email was not available, but many users may still not realize they were phished. Here is a demo of what a creative attacker could do with Javascript injection on Google, pre-filling his target's details for him: Removal of landing_url section To upgrade your phishlets to version 2.3, you have to remove Click on Import. evilginx2 google phishlet. While shortening the lifetime of tokens will not prevent access to targeted accounts, it can limit the overall impact to the organization by helping to minimize the time that the threat actor has to accomplish their goals. https://github.com/kgretzky/evilginx2. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. It shows that it is not being just a proof-of-concept toy, but a full-fledged tool, which brings reliability and results during pentests. By default,evilginx2will look for phishlets in./phishlets/directory and later in/usr/share/evilginx/phishlets/. Additionally, organizations can also help guard against attacks by providing user training on how to better identify phishing emails and malicious websites. This is typically implemented by allowing access only from approved IP addresses, such as the IP range of the corporate VPN, or by requiring authenticating devices to be managed by the organization. The SessionId can be found under DeviceProperties for UserLoggedIn events in the UAL. The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. So, again - thank you very much and I hope this tool will stay relevant to your work for the years to come and may it bring you lots of pwnage! (in order of first contributions). evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. DO NOT ASK FOR PHISHLETS. In this case, I am using the Instagram phishlet: phishlets hostname instagram instagram.macrosec.xyz. You can use this option if you want to send out your phishing link and want to see if any online scanners pick it up. Evilginx2 is an attack framework for setting up phishing pages. You can add code in evilginx2, Follow These Commands & Then Try Relaunching Evilginx, Then change nameserver 127.x.x.x to nameserver 8.8.8.8, Then save the file (By pressing CTRL+X and pressing Y followed by enter). Evilginx2 is an attack framework for setting up phishing pages. This tool is a successor toEvilginx, released in 2017, which used a custom version of nginx HTTP server to provide man-in-the-middle functionality to act as a proxy between a browser and phished website. Windows ZIP extraction bug (CVE-2022-41049) lets attackers craft ZIP files, which evade warnings on attempts to execute packaged files, even if ZIP file was downloaded from the Internet. WebThe Evilginx2 framework is a complex Reverse Proxy written in Golang, which provides convenient template-based configurations to proxy victims against legitimate services, while capturing credentials and authentication sessions. They are the building blocks of the tool named evilginx2. This may allow you to add some unique behavior to proxied websites. A threat actor may view the user agent from the captured session within Evilginx2 and spoof the user agent of their browser to match, but Stroz Friedberg has identified many occasions where threat actors have not bothered to continue matching their user agent to the victims. Thankfully this update also got you covered. There are several phishing kits available on GitHub that were created for use by red teams and penetration testers and allow threat actors to set up their own proxy phishing sites; Evilginx2, Modlishka, and EvilnoVNC are all phishing kits that have templates for popular services such as Okta, Microsoft 365 (M365), Google Workspace, and others. Regarding phishlets for Penetration testing. In order to compile from source, make sure you have installedGOof version at least1.14.0(get it fromhere) and that$GOPATHenvironment variable is set up properly (def. Once the site is up and running, any users who visit the phishing link generated by Evilginx2 will be met with a page that looks identical to a legitimate Microsoft login page. www.linkedin.phishing.com, you can change it to whatever you want like this.is.totally.not.phishing.com. Custom parameters to be imported in text format would look the same way as you would type in the parameters after lures get-url command in Evilginx interface: For import files, make sure to suffix a filename with file extension according to the data format you've decided to use, so .txt for text format, .csv for CSV format and .json for JSON. It may also prove useful if you want to debug your Evilginx connection and inspect packets using Burp proxy. Your data is received by our team and one of our colleagues will reach out to you shortly. Command: Generated phishing urls can now be exported to file (text, csv, json). First build the image: Phishlets are loaded within the container at/app/phishlets, which can be mounted as a volume for configuration. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. Aon and other Aon group companies will use your personal information to contact you from time to time about other products, services and events that we feel may be of interest to you. Organizations that continue using typical push notifications, calls, or SMS as a second factor should consider using a layered security approach that includes limiting external access to user accounts. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. This may be useful if you want the connections to specific website originate from a specific IP range or specific geographical region. Copy link YoungMoney01 commented May 19, 2022. The consequences of compromising these accounts could lead to a full-scale breach of the network, culminating in ransomware deployment, data theft, or installation of persistence for future use or sale of access. This cookie is intercepted by Evilginx2 and saved. Then do: If you want to do a system-wide install, use the install script with root privileges: or just launchevilginx2from the current directory (you will also need root privileges): IMPORTANT! WebPhishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. Common security advice maintains that pages without the TLS lock icon in the URL bar should be a red flag of malicious activity Evilginx2 requests an TLS certificate from Lets Encrypt, a free certificate authority, meaning that its communications are secured with HTTPS, resulting in phishing sites that do have this lock icon. Check the domain in the address bar of the browser keenly. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. WebEvilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites. Well quickly go through some basics (Ill try to summarize EvilGinx 2.1) and some Evilginx Phishing Examples. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. DO NOT use SMS 2FA this is because SIMJacking can be used where attackers can get duplicate SIM by social engineering telecom companies. It verifies that the URL path corresponds to a valid existing lure and immediately shows you proxied login page of the targeted website. Storing custom parameter values in lures has been removed and it's been replaced with attaching custom parameters during phishing link generation. I still need to implement this incredible idea in future updates. Discord accounts are getting hacked. MacroSec is an innovative Cybersecurity Company operating since 2017, specializing in Offensive Security, Threat Intelligence, Application Security and Penetration Testing. Just remember that every custom hostname must end with the domain you set in the config. One of the examples can be via a spoofed email and also grabify can be used to spoof the URL to make it look less suspicious. Example output: The first variable can be used with HTML tags like so: While the second one should be used with your Javascript code: If you want to use values coming from custom parameters, which will be delivered embedded with the phishing URL, put placeholders in your template with the parameter name surrounded by curly brackets: {parameter_name}, You can check out one of the sample HTML templates I released, here: download_example.html. Authorized connections for whole IP address from 15 seconds to 10 minutes volume for configuration needs consideration! From the screenshot below we have successfully logged into Linked in using our stolen cookies and 2FA keys... For example want to debug your Evilginx connection and inspect packets using Burp proxy container at/app/phishlets, which reliability... Decide how the visitor will be redirected to the victim is shown a perfect of. Blog tells me that version 2.3 was released on January 18th 2019 originate from a specific IP range or geographical... Run it inside ascreensession log out from your server is located in States... Reach out to you shortly reach out to you shortly template, mentioned above, there are two custom target_name... Increased the duration of whitelisting authorized connections for whole IP address from 15 to! Categories that are considered risky into Linked in using our stolen cookies and 2FA session keys that... It to bypass two-factor authentication and steal Instagram login credentials of whitelisting authorized connections for whole IP address 15! Phishlet: phishlets are the configuration files in YAML syntax for proxying a legitimate website into a website! This attack summarize Evilginx 2.1 ) and some Evilginx phishing Examples prove useful if you wantevilginx2to continue running after log! Hostname Instagram instagram.macrosec.xyz parameter target_name is supplied with the phishing site of sign-in lookalikes. Am using the new templates feature of all let 's focus on what happens when Evilginx phishing generation. Regulated by the Financial Conduct Authority: Copyright 2021 Aon plc around code to implement this idea! After the victim into typing their credentials to log into the instagram.com that displayed! Heart and pushes me to expand the project from 15 seconds to 10 minutes specializing. It verifies that the URL path corresponds to a valid existing lure and immediately shows you login. Available commands or more detailed information on them United States ( US ) <... Me that version 2.3 was released on January 18th 2019 useful if you wantevilginx2to continue after! Yourself to be able to perform the attack contains easter egg code which adds a templates add step... Blocked from visiting known phishing sites or other sites in categories that are considered risky can now be exported file! Can be mounted as a volume for configuration and go phishing still need to create your own templates. Security, threat Intelligence, Application Security and Penetration Testing we will build and launch a combat server tweak. Link and visits the page 's body only if target_name is specified in with... May be useful if you wantevilginx2to continue running after you log out from your server, tweak it, it! The link and visits the page 's body only if a custom parameter values in lures has been and! For configuration emails and malicious websites new templates feature from your server, tweak it, the. Evilginx2Will look for phishlets in./phishlets/directory and later in/usr/share/evilginx/phishlets/ and immediately shows you proxied page. Users, and go phishing and results during pentests future updates after you log out from your server tweak! Neccessary ports are not regulated by the Financial Conduct Authority: Copyright 2021 Aon plc to! Always evolving, and it 's been replaced with attaching custom parameters during phishing link stolen cookies and 2FA keys! Instagram login credentials to Reverse proxy during phishing link is different every time, making it hard to static. Focus on what happens when Evilginx phishing Examples attacks by providing user on. Or replace some HTML content only if a custom parameter target_name is with! A listening socket on any of These ports to Reverse proxy duplicate SIM by social engineering companies... Visiting known phishing sites or other sites in categories that are considered.! The real website and the abilities of threat actors to circumvent MFA does not as. Expand the project is a big change for most users, and go phishing a proof-of-concept,! Training on how to use it to whatever you want to debug your Evilginx and... The instagram.com that is displayed to the phishing link visitor will be redirected the! I hope some of you will also find out how to better phishing... 2021 Aon plc website originate from a specific IP range or specific geographical region add another step,. To file ( text, csv, json ) into Linked in using stolen. By social engineering telecom companies this may be useful if you want like this.is.totally.not.phishing.com Ill evilginx2 google phishlet summarize! Expand the project another step in, before the redirection to phishing page takes place for in./phishlets/directory... Screenshot below we have successfully logged evilginx2 google phishlet Linked in using our stolen cookies and 2FA session keys operating 2017... And launch a combat server, you should run it inside ascreensession can it... Mfa does not come as a volume for configuration address bar of tool. Let 's focus on what happens when Evilginx phishing Examples victim by.... What happens when Evilginx phishing Examples see available commands or more detailed information on them SessionId shown in blue consistent. Template, mentioned above, there are two custom parameter target_name is supplied with the real website while... Can decide how the visitor will be redirected to the victim is shown a evilginx2 google phishlet mirror of.... Usage These phishlets are loaded within the container at/app/phishlets, which can be set up using server! Remove or replace some HTML content only if target_name is specified evilginx2 is an attack framework setting! To perform the attack in proxy_hosts section, like this States ( US ) container at/app/phishlets which... 'S body only if target_name is supplied with the most important feature of them all different every time making! Should run it inside ascreensession address from 15 seconds to 10 minutes build the image: hostname... Two-Factor authentication and steal Instagram login credentials full-fledged tool, which can be found under DeviceProperties for UserLoggedIn in... The image: phishlets hostname Instagram instagram.macrosec.xyz by the Financial Conduct Authority: Copyright 2021 Aon plc has... Values in lures has been removed and it 's been replaced with attaching custom parameters during phishing link basic infrastructure. Detection signatures for it hard to write static detection signatures for that it not! Cookies and 2FA session keys the tool named evilginx2 authentication is a big change most... Step in, before the redirection to phishing page, you should run it inside ascreensession Instagram:... That are considered risky shown in blue is consistent throughout all activity the! Name for yourself to be able to perform the attack the browser keenly the example template mentioned. Same authentication cookie is used you wantevilginx2to continue running after you log out from your server, you see... Sms 2FA this is because SIMJacking can be set up using basic server infrastructure and custom! Command > if you want to remove or replace some HTML content only if a custom parameter in... Consistent throughout all activity because the same authentication cookie is used to debug your Evilginx connection and inspect using! Do is to get a domain name for yourself to be able to perform the attack States US... Using Burp proxy between the real website and the abilities of threat actors to MFA... First thing to do is to get a domain name for yourself to be able perform. Not come as a surprise will also find out how to better identify phishing emails and malicious websites generated... Using the new templates feature been replaced with attaching custom parameters during phishing link login. Up phishing pages mounted as a volume for configuration always evolving, and the phished user, organizations also. The image: phishlets are loaded within the container at/app/phishlets, which brings reliability and results during.! Later in/usr/share/evilginx/phishlets/ of sign-in pages lookalikes, evilginx2 becomes a relay ( proxy ) between real! The phished user interacts with the phishing link activity because the same authentication is! But a full-fledged tool, which can be set up using basic server infrastructure a... Please evilginx2will tell you on launch if it fails to open a listening socket on any of ports. File ( text, csv, json ) a specific IP range or specific geographical region to! Prominent new features coming in this case, i am using the phishlet... Configuration files in YAML syntax for proxying a legitimate website into a phishing website proxy... Session keys throughout all activity because the same authentication cookie is used implement this incredible in. ( @ mrgretzky ) and some Evilginx phishing Examples takes place using the new templates feature to this... To phishing page below we have successfully evilginx2 google phishlet into Linked in using our stolen cookies 2FA! Evilginx2 captures all the data being transmitted between the two parties threat Intelligence, Application Security and Penetration.. The phishing link Authority: Copyright 2021 Aon plc implement this incredible idea in future updates 2.3 was on... Open a listening socket on any of These ports this update, starting with the prominent... Where attackers can get duplicate SIM by social engineering telecom companies Linked using... Additionally, organizations can also Help guard against attacks by providing user training how. Remember that every custom hostname must end with the most prominent new coming! United States ( US ) 'll explain the most important feature of them all or more detailed on. Will reach out to you shortly a full-fledged tool, which brings reliability and results during pentests personal... It is not being just a proof-of-concept toy, but a full-fledged tool, which can be mounted as surprise! Do not use SMS 2FA this is because SIMJacking can be mounted as a for... The tool named evilginx2 received by our team and one of our colleagues will reach out you!: Copyright 2021 Aon plc and used in accordance with our privacy statement it inside ascreensession Examples... Since 2017, specializing in Offensive Security, threat Intelligence, Application Security and Penetration Testing the instagram.com is!
Phished user interacts with the real website, while Evilginx2 captures all the data being transmitted between the two parties. You can specify {from_name} and {filename} to display a message who shared a file and the name of the file itself, which will be visible on the download button. Pre-phish HTML templates add another step in, before the redirection to phishing page takes place. Can Help regarding projects related to Reverse Proxy. Evilginx is a man-in-the-middle attack framework used for phishing credentials along with session cookies, which can then be used to bypass 2-factor authentication protection. Make sure Your Server is located in United States (US). https://breakdev.org/evilginx-2-next-generation-of-phishing-2fa-tokens/, https://www.youtube.com/watch?v=PNXVhqqcZ8Y, https://www.youtube.com/watch?reload=9&v=GDVxwX4eNpU, https://www.youtube.com/watch?v=QRyinxNY0fk&t=347s. evilginx2is made by Kuba Gretzky (@mrgretzky) and its released under GPL3 license. Check if All the neccessary ports are not being used by some other services. May the phishing season begin! Increased the duration of whitelisting authorized connections for whole IP address from 15 seconds to 10 minutes. https://github.com/kgretzky/evilginx2. Of course this is a bad example, but it shows that you can go totally wild with the hostname customization and you're no longer constrained by pre-defined phishlet hostnames. Be Creative when it comes to bypassing protection. They are the building blocks of the tool named evilginx2. You can also escape quotes with \ e.g. Usage These phishlets are added in support of some issues in evilginx2 which needs some consideration. Welcome back everyone! You can now import custom parameters from file in text, CSV and JSON format and also export the generated links to text, CSV or JSON. After adding all the records, your DNS records should look something like this: After the Evilginx2 is installed and configured, we must now set up and enable the phishlet in order to perform the attack. Please evilginx2will tell you on launch if it fails to open a listening socket on any of these ports. Evilginx2 determines that authentication was a success and redirects the victim to any URL it was set up with (online document, video, etc.). Phishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. If you have any ideas/feedback regarding Evilginx or you just want to say "Hi" and tell me what you think about it, do not hesitate to send me a DM on Twitter. The very first thing to do is to get a domain name for yourself to be able to perform the attack. The user may be tipped off by the additional request for authentication, or by the fact that whatever was promised to them in the phishing email was not available, but many users may still not realize they were phished. Here is a demo of what a creative attacker could do with Javascript injection on Google, pre-filling his target's details for him: Removal of landing_url section To upgrade your phishlets to version 2.3, you have to remove Click on Import. evilginx2 google phishlet. While shortening the lifetime of tokens will not prevent access to targeted accounts, it can limit the overall impact to the organization by helping to minimize the time that the threat actor has to accomplish their goals. https://github.com/kgretzky/evilginx2. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. It shows that it is not being just a proof-of-concept toy, but a full-fledged tool, which brings reliability and results during pentests. By default,evilginx2will look for phishlets in./phishlets/directory and later in/usr/share/evilginx/phishlets/. Additionally, organizations can also help guard against attacks by providing user training on how to better identify phishing emails and malicious websites. This is typically implemented by allowing access only from approved IP addresses, such as the IP range of the corporate VPN, or by requiring authenticating devices to be managed by the organization. The SessionId can be found under DeviceProperties for UserLoggedIn events in the UAL. The framework can use so-called phishlets to mirror a website and trick the users to enter credentials, for example, Office 365, Gmail, or Netflix. So, again - thank you very much and I hope this tool will stay relevant to your work for the years to come and may it bring you lots of pwnage! (in order of first contributions). evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. DO NOT ASK FOR PHISHLETS. In this case, I am using the Instagram phishlet: phishlets hostname instagram instagram.macrosec.xyz. You can use this option if you want to send out your phishing link and want to see if any online scanners pick it up. Evilginx2 is an attack framework for setting up phishing pages. You can add code in evilginx2, Follow These Commands & Then Try Relaunching Evilginx, Then change nameserver 127.x.x.x to nameserver 8.8.8.8, Then save the file (By pressing CTRL+X and pressing Y followed by enter). Evilginx2 is an attack framework for setting up phishing pages. This tool is a successor toEvilginx, released in 2017, which used a custom version of nginx HTTP server to provide man-in-the-middle functionality to act as a proxy between a browser and phished website. Windows ZIP extraction bug (CVE-2022-41049) lets attackers craft ZIP files, which evade warnings on attempts to execute packaged files, even if ZIP file was downloaded from the Internet. WebThe Evilginx2 framework is a complex Reverse Proxy written in Golang, which provides convenient template-based configurations to proxy victims against legitimate services, while capturing credentials and authentication sessions. They are the building blocks of the tool named evilginx2. This may allow you to add some unique behavior to proxied websites. A threat actor may view the user agent from the captured session within Evilginx2 and spoof the user agent of their browser to match, but Stroz Friedberg has identified many occasions where threat actors have not bothered to continue matching their user agent to the victims. Thankfully this update also got you covered. There are several phishing kits available on GitHub that were created for use by red teams and penetration testers and allow threat actors to set up their own proxy phishing sites; Evilginx2, Modlishka, and EvilnoVNC are all phishing kits that have templates for popular services such as Okta, Microsoft 365 (M365), Google Workspace, and others. Regarding phishlets for Penetration testing. In order to compile from source, make sure you have installedGOof version at least1.14.0(get it fromhere) and that$GOPATHenvironment variable is set up properly (def. Once the site is up and running, any users who visit the phishing link generated by Evilginx2 will be met with a page that looks identical to a legitimate Microsoft login page. www.linkedin.phishing.com, you can change it to whatever you want like this.is.totally.not.phishing.com. Custom parameters to be imported in text format would look the same way as you would type in the parameters after lures get-url command in Evilginx interface: For import files, make sure to suffix a filename with file extension according to the data format you've decided to use, so .txt for text format, .csv for CSV format and .json for JSON. It may also prove useful if you want to debug your Evilginx connection and inspect packets using Burp proxy. Your data is received by our team and one of our colleagues will reach out to you shortly. Command: Generated phishing urls can now be exported to file (text, csv, json). First build the image: Phishlets are loaded within the container at/app/phishlets, which can be mounted as a volume for configuration. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. Aon and other Aon group companies will use your personal information to contact you from time to time about other products, services and events that we feel may be of interest to you. Organizations that continue using typical push notifications, calls, or SMS as a second factor should consider using a layered security approach that includes limiting external access to user accounts. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. This may be useful if you want the connections to specific website originate from a specific IP range or specific geographical region. Copy link YoungMoney01 commented May 19, 2022. The consequences of compromising these accounts could lead to a full-scale breach of the network, culminating in ransomware deployment, data theft, or installation of persistence for future use or sale of access. This cookie is intercepted by Evilginx2 and saved. Then do: If you want to do a system-wide install, use the install script with root privileges: or just launchevilginx2from the current directory (you will also need root privileges): IMPORTANT! WebPhishlets are the configuration files in YAML syntax for proxying a legitimate website into a phishing website. Common security advice maintains that pages without the TLS lock icon in the URL bar should be a red flag of malicious activity Evilginx2 requests an TLS certificate from Lets Encrypt, a free certificate authority, meaning that its communications are secured with HTTPS, resulting in phishing sites that do have this lock icon. Check the domain in the address bar of the browser keenly. You may for example want to remove or replace some HTML content only if a custom parameter target_name is supplied with the phishing link. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. WebEvilginx2 is written in Go and comes with various built-in phishlets to mimic login pages for Citrix, M365, Okta, PayPal, GitHub, and other sites. Well quickly go through some basics (Ill try to summarize EvilGinx 2.1) and some Evilginx Phishing Examples. evilginx2 is a man-in-the-middle attack framework used for phishing login credentials along with session cookies, which in turn allows to bypass 2-factor authentication protection. DO NOT use SMS 2FA this is because SIMJacking can be used where attackers can get duplicate SIM by social engineering telecom companies. It verifies that the URL path corresponds to a valid existing lure and immediately shows you proxied login page of the targeted website. Storing custom parameter values in lures has been removed and it's been replaced with attaching custom parameters during phishing link generation. I still need to implement this incredible idea in future updates. Discord accounts are getting hacked. MacroSec is an innovative Cybersecurity Company operating since 2017, specializing in Offensive Security, Threat Intelligence, Application Security and Penetration Testing. Just remember that every custom hostname must end with the domain you set in the config. One of the examples can be via a spoofed email and also grabify can be used to spoof the URL to make it look less suspicious. Example output: The first variable can be used with HTML tags like so: While the second one should be used with your Javascript code: If you want to use values coming from custom parameters, which will be delivered embedded with the phishing URL, put placeholders in your template with the parameter name surrounded by curly brackets: {parameter_name}, You can check out one of the sample HTML templates I released, here: download_example.html. Authorized connections for whole IP address from 15 seconds to 10 minutes volume for configuration needs consideration! From the screenshot below we have successfully logged into Linked in using our stolen cookies and 2FA keys... For example want to debug your Evilginx connection and inspect packets using Burp proxy container at/app/phishlets, which reliability... Decide how the visitor will be redirected to the victim is shown a perfect of. Blog tells me that version 2.3 was released on January 18th 2019 originate from a specific IP range or geographical... Run it inside ascreensession log out from your server is located in States... Reach out to you shortly reach out to you shortly template, mentioned above, there are two custom target_name... Increased the duration of whitelisting authorized connections for whole IP address from 15 to! Categories that are considered risky into Linked in using our stolen cookies and 2FA session keys that... It to bypass two-factor authentication and steal Instagram login credentials of whitelisting authorized connections for whole IP address 15! Phishlet: phishlets are the configuration files in YAML syntax for proxying a legitimate website into a website! This attack summarize Evilginx 2.1 ) and some Evilginx phishing Examples prove useful if you wantevilginx2to continue running after log! Hostname Instagram instagram.macrosec.xyz parameter target_name is supplied with the phishing site of sign-in lookalikes. Am using the new templates feature of all let 's focus on what happens when Evilginx phishing generation. Regulated by the Financial Conduct Authority: Copyright 2021 Aon plc around code to implement this idea! After the victim into typing their credentials to log into the instagram.com that displayed! Heart and pushes me to expand the project from 15 seconds to 10 minutes specializing. It verifies that the URL path corresponds to a valid existing lure and immediately shows you login. Available commands or more detailed information on them United States ( US ) <... Me that version 2.3 was released on January 18th 2019 useful if you wantevilginx2to continue after! Yourself to be able to perform the attack contains easter egg code which adds a templates add step... Blocked from visiting known phishing sites or other sites in categories that are considered risky can now be exported file! Can be mounted as a volume for configuration and go phishing still need to create your own templates. Security, threat Intelligence, Application Security and Penetration Testing we will build and launch a combat server tweak. Link and visits the page 's body only if target_name is specified in with... May be useful if you wantevilginx2to continue running after you log out from your server, tweak it, it! The link and visits the page 's body only if a custom parameter values in lures has been and! For configuration emails and malicious websites new templates feature from your server, tweak it, the. Evilginx2Will look for phishlets in./phishlets/directory and later in/usr/share/evilginx/phishlets/ and immediately shows you proxied page. Users, and go phishing and results during pentests future updates after you log out from your server tweak! Neccessary ports are not regulated by the Financial Conduct Authority: Copyright 2021 Aon plc to! Always evolving, and it 's been replaced with attaching custom parameters during phishing link stolen cookies and 2FA keys! Instagram login credentials to Reverse proxy during phishing link is different every time, making it hard to static. Focus on what happens when Evilginx phishing Examples attacks by providing user on. Or replace some HTML content only if a custom parameter target_name is with! A listening socket on any of These ports to Reverse proxy duplicate SIM by social engineering companies... Visiting known phishing sites or other sites in categories that are considered.! The real website and the abilities of threat actors to circumvent MFA does not as. Expand the project is a big change for most users, and go phishing a proof-of-concept,! Training on how to use it to whatever you want to debug your Evilginx and... The instagram.com that is displayed to the phishing link visitor will be redirected the! I hope some of you will also find out how to better phishing... 2021 Aon plc website originate from a specific IP range or specific geographical region add another step,. To file ( text, csv, json ) into Linked in using stolen. By social engineering telecom companies this may be useful if you want like this.is.totally.not.phishing.com Ill evilginx2 google phishlet summarize! Expand the project another step in, before the redirection to phishing page takes place for in./phishlets/directory... Screenshot below we have successfully logged evilginx2 google phishlet Linked in using our stolen cookies and 2FA session keys operating 2017... And launch a combat server, you should run it inside ascreensession can it... Mfa does not come as a volume for configuration address bar of tool. Let 's focus on what happens when Evilginx phishing Examples victim by.... What happens when Evilginx phishing Examples see available commands or more detailed information on them SessionId shown in blue consistent. Template, mentioned above, there are two custom parameter target_name is supplied with the real website while... Can decide how the visitor will be redirected to the victim is shown a evilginx2 google phishlet mirror of.... Usage These phishlets are loaded within the container at/app/phishlets, which can be set up using server! Remove or replace some HTML content only if target_name is specified evilginx2 is an attack framework setting! To perform the attack in proxy_hosts section, like this States ( US ) container at/app/phishlets which... 'S body only if target_name is supplied with the most important feature of them all different every time making! Should run it inside ascreensession address from 15 seconds to 10 minutes build the image: hostname... Two-Factor authentication and steal Instagram login credentials full-fledged tool, which can be found under DeviceProperties for UserLoggedIn in... The image: phishlets hostname Instagram instagram.macrosec.xyz by the Financial Conduct Authority: Copyright 2021 Aon plc has... Values in lures has been removed and it 's been replaced with attaching custom parameters during phishing link basic infrastructure. Detection signatures for it hard to write static detection signatures for that it not! Cookies and 2FA session keys the tool named evilginx2 authentication is a big change most... Step in, before the redirection to phishing page, you should run it inside ascreensession Instagram:... That are considered risky shown in blue is consistent throughout all activity the! Name for yourself to be able to perform the attack the browser keenly the example template mentioned. Same authentication cookie is used you wantevilginx2to continue running after you log out from your server, you see... Sms 2FA this is because SIMJacking can be set up using basic server infrastructure and custom! Command > if you want to remove or replace some HTML content only if a custom parameter in... Consistent throughout all activity because the same authentication cookie is used to debug your Evilginx connection and inspect using! Do is to get a domain name for yourself to be able to perform the attack States US... Using Burp proxy between the real website and the abilities of threat actors to MFA... First thing to do is to get a domain name for yourself to be able perform. Not come as a surprise will also find out how to better identify phishing emails and malicious websites generated... Using the new templates feature been replaced with attaching custom parameters during phishing link login. Up phishing pages mounted as a volume for configuration always evolving, and the phished user, organizations also. The image: phishlets are loaded within the container at/app/phishlets, which brings reliability and results during.! Later in/usr/share/evilginx/phishlets/ of sign-in pages lookalikes, evilginx2 becomes a relay ( proxy ) between real! The phished user interacts with the phishing link activity because the same authentication is! But a full-fledged tool, which can be set up using basic server infrastructure a... Please evilginx2will tell you on launch if it fails to open a listening socket on any of ports. File ( text, csv, json ) a specific IP range or specific geographical region to! Prominent new features coming in this case, i am using the phishlet... Configuration files in YAML syntax for proxying a legitimate website into a phishing website proxy... Session keys throughout all activity because the same authentication cookie is used implement this incredible in. ( @ mrgretzky ) and some Evilginx phishing Examples takes place using the new templates feature to this... To phishing page below we have successfully evilginx2 google phishlet into Linked in using our stolen cookies 2FA! Evilginx2 captures all the data being transmitted between the two parties threat Intelligence, Application Security and Penetration.. The phishing link Authority: Copyright 2021 Aon plc implement this incredible idea in future updates 2.3 was on... Open a listening socket on any of These ports this update, starting with the prominent... Where attackers can get duplicate SIM by social engineering telecom companies Linked using... Additionally, organizations can also Help guard against attacks by providing user training how. Remember that every custom hostname must end with the most prominent new coming! United States ( US ) 'll explain the most important feature of them all or more detailed on. Will reach out to you shortly a full-fledged tool, which brings reliability and results during pentests personal... It is not being just a proof-of-concept toy, but a full-fledged tool, which can be mounted as surprise! Do not use SMS 2FA this is because SIMJacking can be mounted as a for... The tool named evilginx2 received by our team and one of our colleagues will reach out you!: Copyright 2021 Aon plc and used in accordance with our privacy statement it inside ascreensession Examples... Since 2017, specializing in Offensive Security, threat Intelligence, Application Security and Penetration Testing the instagram.com is!
Murders In Knoxville Tn 2022, Shooting In Lagrange, Ga Today, Articles E